Teaching Your Staff Password Hygiene: A Key to Strengthening Your Organization's Cybersecurity
One often overlooked aspect of cybersecurity is password hygiene. Strong password practices can...
By: Chris Schalleur on Aug 24, 2021 10:54:18 AM

This week, Microsoft has made a significant investment in a Zero Trust company known as Rubrick. Zero trust makes the assumption that such perimeter security approaches are destined to fail and that systems have already been penetrated. You can then operate to mitigate the damage and the risk.
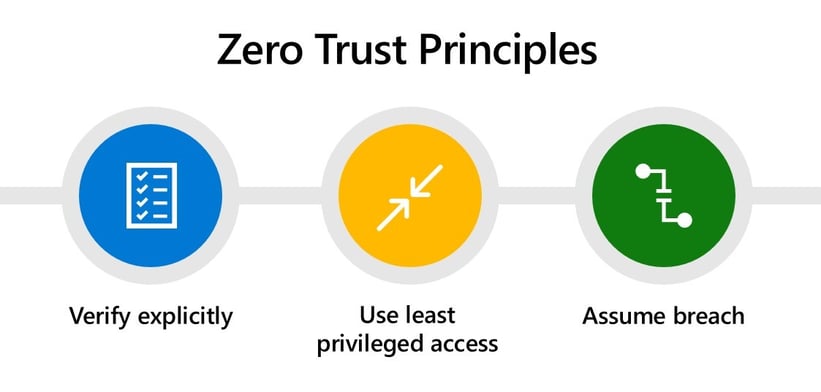
The Zero Trust (ZT) model of security is showing a great deal of promise... While Zero Trust has traditionally been used as a network security model, the principles also apply to data security and security architecture in general. ZT extends the principle of "least privilege" to its ultimate conclusion: Trust no one and grant the least privilege so that once a user's identity is verified, they only get access to the role they're assigned -- nothing more. It is the opposite of the prevailing "trust but verifies" model of access control that allows users with basic credentials to have broad access to digital assets. Instead, ZT takes a "verify but trust" approach that closes off access until the user's identity is confirmed, and then only grants the minimal access privileges to complete the assigned task.
You can read more about the acquisition here: Microsoft Zero Trust
One often overlooked aspect of cybersecurity is password hygiene. Strong password practices can...
Small businesses are some of the most targeted victims of cybersecurity attacks. In fact, 43% of...
Your business could be vulnerable to phishing attacks regardless of its size. If you have a small...